Features
Polar Crypto is the premium data protection tool for software developers. It supports the securest, most recommended, and most up-to-date cryptographic standards and crypto systems.

The power of Polar Crypto Component is manifested in this list of its many advanced features
Polar Crypto features the latest encryption technology and is the premium data protection tool for software developers.
Features
- Full source code
- Encryption/Decryption
- Digital signature
- Hash generation
- Streaming
- Random Generator
- Tools
- General process information
Polar Crypto object model
Features
1. Full source code included
- Completely written in Microsoft Visual C++
- Choose between component and source code when implementing Polar Crypto into your application;
- You can further develop and / or customize the products;
- It is included at the regular component price;Source code license agreement
2. Encryption/Decryption
- Encrypt files, strings, buffers (Encrypt Method, Decrypt Method)
- Use symmetric (AES and Twofish) or asymmetric keys (RSA)
- Use public and private RSA keys for encryption/decryption
- 128 to 256-bit symmetric keys for AES and Twofish
- 512, 1024 and 2048-bit keys for asymmetric RSA encryption
3. Digital signature
- Sign your data with the RSA private key (Sign Method)
- Verify signed data (VerifySignature Method)
4. Hash generation
- Produce a hash value using the SHA-1 & SHA-2 algorithms
5. Streaming
- Set the Streaming Property to TRUE if you do not have a single data block
6. Random Generator
- Use the built-in random data generator (Blum, Blum and Shub algorithm)
- Set your own seed for an algorithm (RandomGeneratorSeed Property)
7. Tools
- Convert your data to the Base64 or Hex format with the CryptoData Object
- Manipulate the original binary data
8. General process information
- Use the OnError Event to detect any errors in the encryption/decryption process
- ProcessingStatus Event will tell you the current status of the operation
Polar Crypto object model
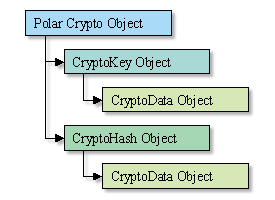
1. Crypto object
The Crypto object represents the control itself. It can be used for creating/exporting/importing the keys and creating the hash.
Properties
- AllowErrorReporting Property
- ObjectType Property
- RandomGeneratorSeed PropertyMethods
- CreateHash Method
- DeriveKey Method
- ForceKey Method
- GenerateKey Method
- GenerateRandomData Method
- ImportKey MethodEvents
- OnError Event
- ProcessingEnded Event
- ProcessingStarted Event
- ProcessingStatus Event
2. CryptoKey Object
The CryptoKey object encapsulates the encryption and decryption key and performs all encryption/decryption, data hashing and signing operations.
Properties
- CipherMode Property
- EncryptionScheme Property
- InitializationVector Property
- Length Property
- ObjectType Property
- Padding Property
- Type PropertyMethods
- CalculateHash Method
- Decrypt Method
- DecryptFile Method
- Destroy Method
- Encrypt Method
- EncryptFile Method
- Export Method
- Sign Method
- SignHash Method
- VerifySignature Method
3. Hash Object
This object is used for hashing data.
Properties
- ObjectType Property
- Value Property
- Lenght PropertyMethods
- AddData Method
- AddFile Method
- Destroy Method
- Duplicate Method
4. CryptoData Object
The CyrptoData object is used for data manipulation such as conversion, encoding and decoding, reading and writing to disk.
Properties
- Length Property
- ObjectType Property
- Streaming Property
- Value PropertyMethods
- Compare Method
- FromBlob Method
- FromBuffer Method
- FromString Method
- ReadFromFile Method
- ToBlob Method
- ToBuffer Method
- ToString Method
- WriteToFile Method
5. List of enumerations
- pcaAlgorithms Enumeration
- pceErrorConstants Enumeration
- pceRSAExportType Enumeration
- pcfEncodingFormat Enumeration
- pchHashSize Enumeration
- pclKeyLength Enumeration
- pcmCipherMode Enumeration
- pcmProcessingMode Enumeration
- pcoObjectType Enumeration
- pcpPadding Enumeration
- pcsEncryptionScheme Enumeration
